Understanding how SHA256 helps Bitcoin secure billions of dollars of value
It has been over 14 years since Bitcoin’s whitepaper was first released. Shortly following this release, the network underpinning the original cryptocurrency was launched. Since that moment, many people have come to understand Bitcoin to varying degrees of proficiency. Bitcoin’s consensus mechanism, called proof-of-work (PoW), is the most misunderstood piece of Bitcoin’s technology stack, especially because it is usually explained badly.
As Bitcoin grows, concerns rise over its energy consumption and its place in global financial infrastructure. These concerns typically emerge from a misunderstanding of the key consensus system underpinning the Bitcoin network. They also lead to calls for a change to its underlying consensus system to be more energy efficient. However, those that call for such transitions rarely understand the security tradeoffs with alternative consensus systems such as proof-of-stake.
Understanding the full technical design of PoW is hard. But understanding the basic tenets of PoW will help people truly understand the potential and position of Bitcoin in a rapidly evolving globalized economy. In this Asic Jungle overview, we will detail how the PoW mechanism underpinning Bitcoin’s security actually works.
The foundations of proof-of-work Bitcoin mining
The security and consensus of the Bitcoin network are underpinned by what is called an SHA-256 hashing algorithm. Miners worldwide are competing to solve these hashing algorithms as quickly as possible to append blocks to the Bitcoin blockchain. Miners put various input variables through the SHA-256 hashing algorithm and if they reach an output that meets predetermined conditions, they can append a block and receive the block reward associated.
But not every output meets those predetermined conditions. Any given miner typically completes these hash equations several trillion times per second in an attempt to meet the predetermined conditions. On a whole, Bitcoin miners across the globe are currently hashing the equation roughly 257 quintillion times per second. The beauty of the system is in its adaptive mechanism and difficulty level. If miners are appending blocks faster than every ten minutes, the difficulty to find the predetermined output increases. If miners are appending blocks slower than 10 minutes, the difficulty will drop. This difficulty adjustment takes place every 2016th block (roughly two weeks).
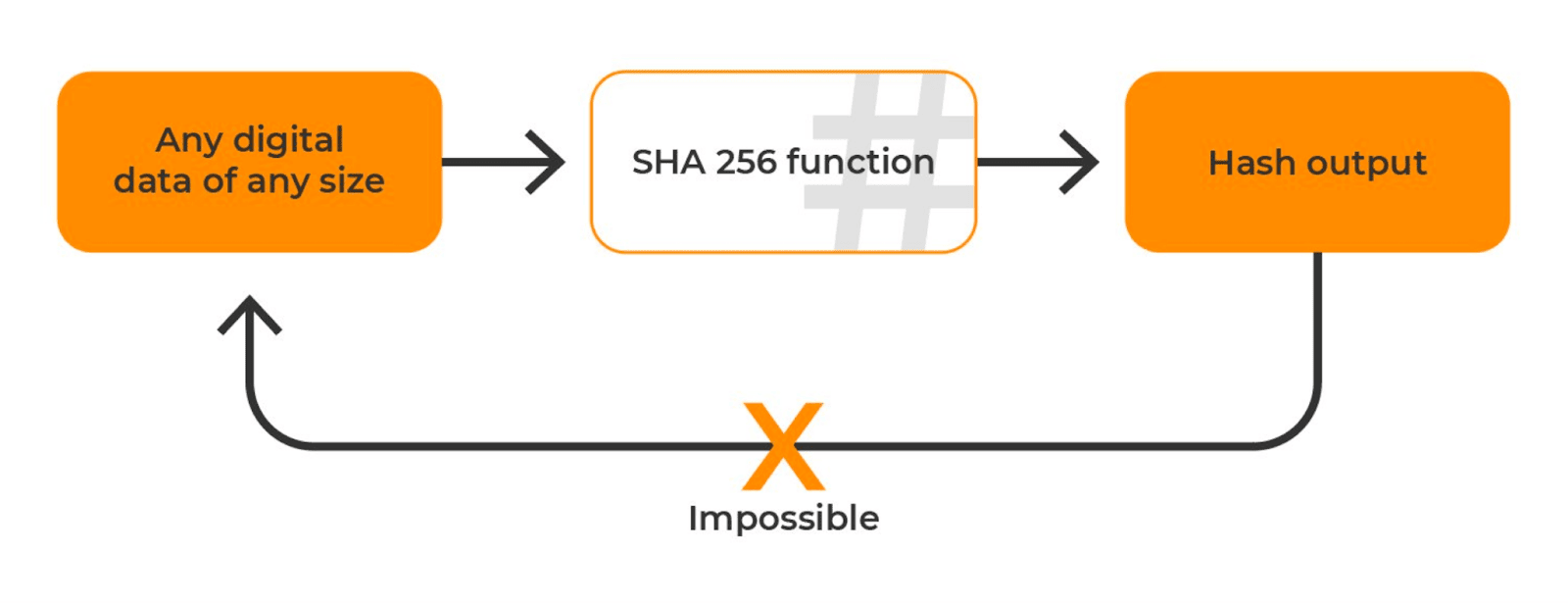
The SHA-256 hashing algorithm is a special type of cryptographic function usually called one-way functions. These functions are special because they are random yet deterministic, irreversible yet repeatable. Before you introduce the input into the algorithm, you don’t know what you will get, but every time you introduce the same input, you will get the same output.
(Source: armantheparman.com)
On the other hand, if someone only had the output, it would be absolutely impossible to know what the input was without previous knowledge. It is also important to note that each output can be expressed as a number between 1 and 2256. This means that every time you introduce an input, you will get a number, at random, between the previous ones as an output.
When we put this information together, we can see that miners are essentially taking input variables and computing them as many times as possible per second to find an output that meets what is called the golden nonce - an output that meets the minimum level of difficulty required. The nonce is one of the variables which is included in the hashing algorithm and a golden nonce is one that meets the mining requirements to add a block.
Exploring the variables that go into each Bitcoin block
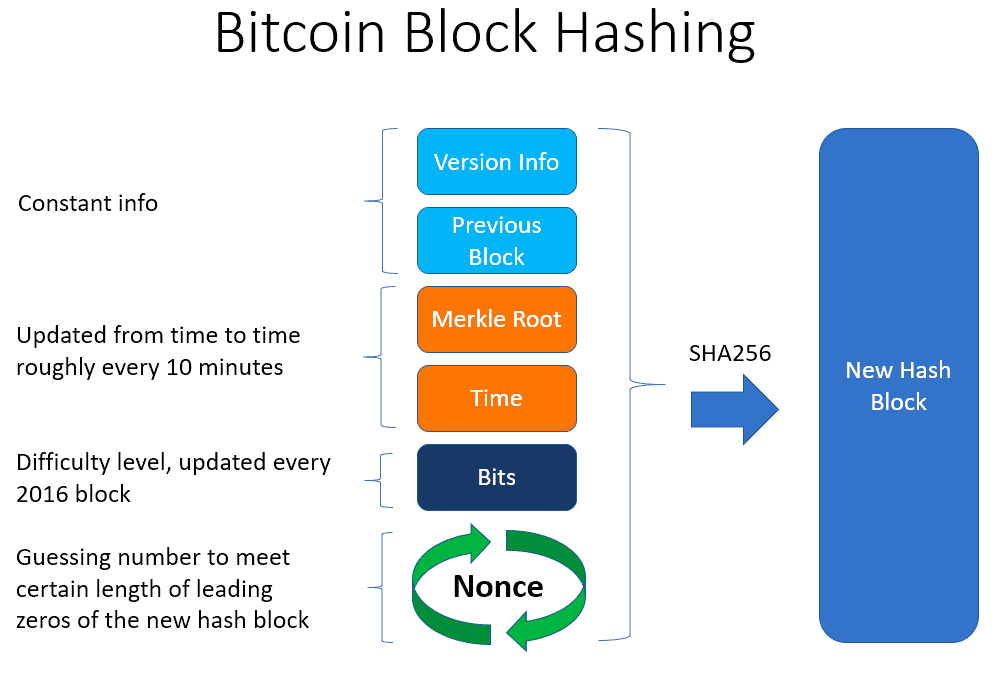
Let’s dive deeper into the input variables that are hashed in an attempt to meet the output with the golden nonce. Together, these input variables can be called the block header. The block header is one of the components of a Bitcoin block with the other part being the transactions. This block header is a compressed version of the entire block, and it contains six separate pieces of information:
- Bitcoin Version
- Previous Block Header
- Merkle Root
- Timestamp
- Bits (Compressed Difficulty Target)
- Nonce
Bitcoin Version: Includes current Bitcoin software version.
Previous Block Header: The field of the block header where miners have to introduce the hash or solution of the previous block header. This is done in order to cryptographically ingrain the previous block into the next one, thus creating a chain of blocks. Hence the name of Bitcoin’s underlying technology, Blockchain.
Merkle Root: The Merkle Root is the name of a sophisticated and highly useful cryptographic tool. The Merkle root is like a cryptographic zip file of all the transactions contained in the block. It manages to compress as many transactions as required into a single SHA-256 hash output, thus dramatically reducing the weight. The Merkle Root is very useful in making sure Bitcoin’s blockchain can securely scale.
Timestamp: Records the time at which any Bitcoin block will be added. This also enables Bitcoin to act as a decentralized global clock which can lead to some interesting thought experiments explored here.
Bits: Bits are the compressed way of storing the widely known Difficulty. The Difficulty is the predetermined condition that defines which hashes deserve a block reward.
Nonce: A random number that allows miners to vary their guesses in an attempt to reach the output with a golden nonce. The output with the golden nonce will have a fixed number of zeros at the start of it. The higher the difficulty, the greater the zeros, and the harder it is for the miner to hash an output with a greater number of zeros.
(Source: themoneymongers.com)
ASICs – The evolution of proof-of-work mining
In the PoW mechanism, every hash could be the winning one. The more hash power miners control, the greater the chances of them finding the winning output. This has evolved into a hardware arms race where miners are deploying highly specialized computers called Application Specific Integrated Circuits (ASICs) that can solely be used to mine Bitcoin. Manufacturers are also competing to develop more and more efficient and powerful Bitcoin ASICs. The latest-gen Bitcoin ASIC can currently compute 253 trillion hashes per second. This is a big jump from CPU mining which could only compute between 8 and 20 thousand hashes per second.
With more powerful mining hardware in the pipeline, the number of hashes being computed by miners is set to further increase in the years to come. However, on the other end, Bitcoin’s adaptive mechanism in the difficulty adjustment will ensure that Bitcoin blocks come at a steady rate of 10 minutes per block. This innovative process of PoW mining will continue undeterred and the incentives of the system will ensure that manufacturers continue to develop more powerful hashing hardware that miners themselves will seek to maximize their chances of appending blocks with the golden nonce.






